The A to Z of Cyber Attacks
Cybersecurity: Cyber Attacks in Cyber Space
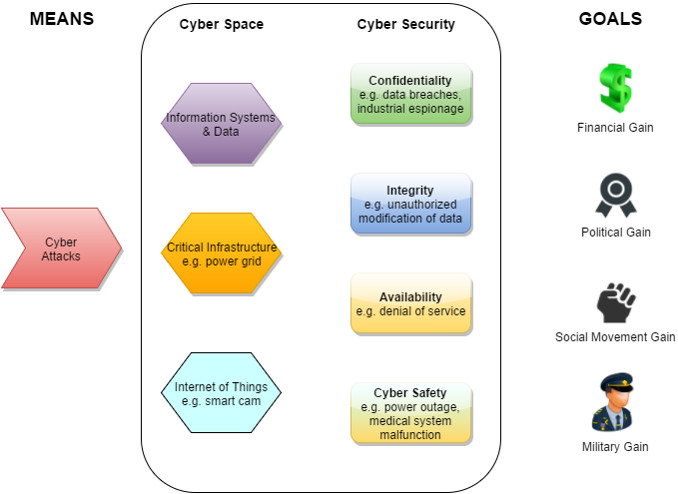
A cyber attack adversely affects (1) information systems & their data, (2) critical infrastructure (e.g. power grid, nuclear plant, etc.), and (3) internet of things. Cybersecurity involves protecting confidentiality, availability, integrity and cyber safety of systems, data and people.
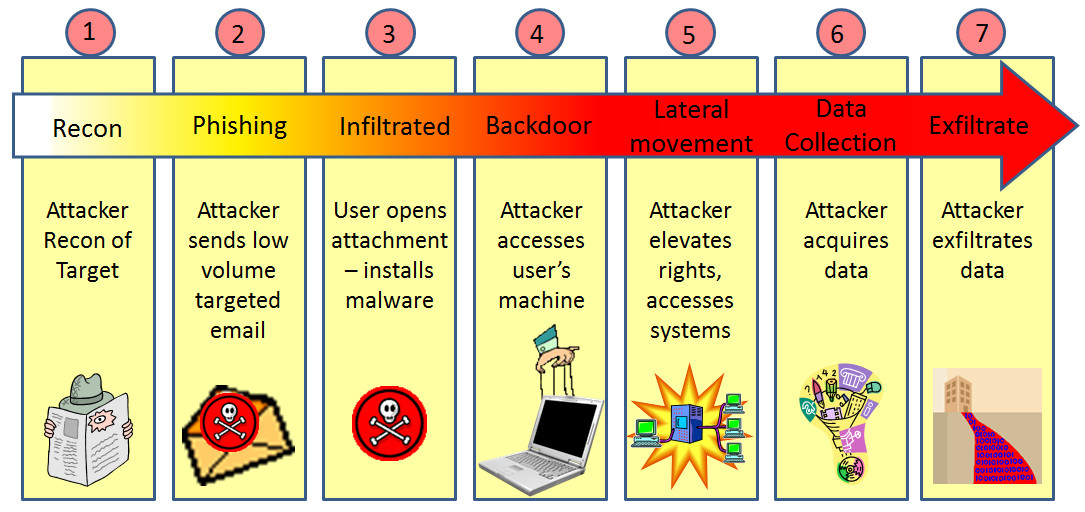
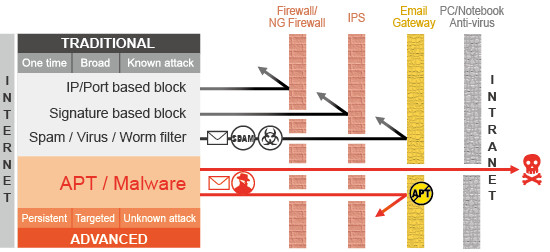
APT Attack
An advanced persistent threat (APT) uses multiple phases to break into a network, avoid detection, and harvest valuable information over the long term.
Bait & Switch Attack
Bait and switch hacking is a technique on the rise due to the explosion of internet-based content marketing. A bait and switch attack occurs when victims are told they are downloading or running a piece of safe and legitimate content or advertising which is then switched (usually by way of a redirect) to something malicious.

Business Email Compromise
Business Email Compromise (BEC) is a sophisticated scam targeting businesses working with foreign suppliers and businesses that regularly transfer payments.
BEC Version 1
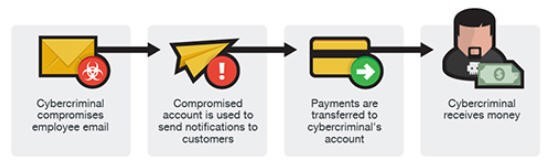
BEC Version 2
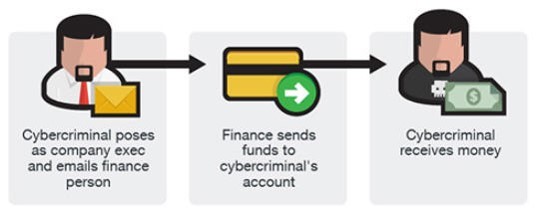
BEC Version 3
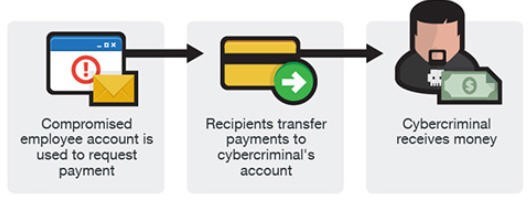
Distributed Denial of Service Attack
It is a cyber attack to make an online service unavailable by overwhelming it with traffic from multiple sources.
a) Volumetric Attacks --- all kinds of flooding patterns through self-built botnet, rental DDoS service, reflective / amplification DDoS techniques through public DNS, NTP services;
b) Low and Slow Attacks --- exhaust concurrent sessions and new sessions of core network devices in light and slow manner;
c) Application Attacks --- through repeated login attempts, repeated application service requests, etc.;
d) Database Attacks --- through repeated database service requests

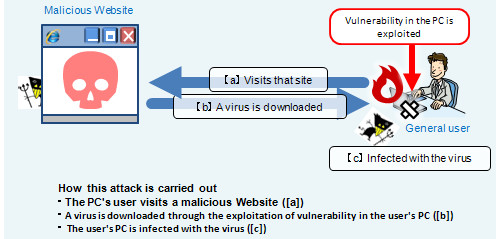
Drive-by Attack
Web sites designed or compromised to install malicious code on web visitors' PCs
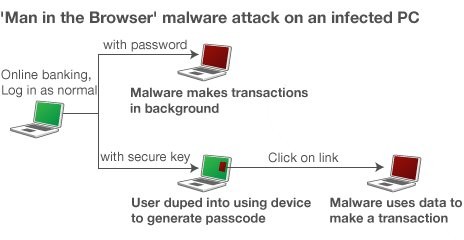
Man in the Browser Attack
An attacker intercepts messages in a public key exchange. The attacker then retransmits the messages, substituting bogus public keys for the requested ones with the aim of obtaining sensitive information from the sending party.
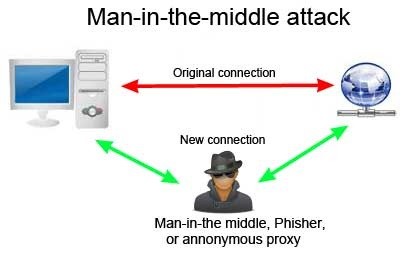
Man in the Middle Attack
A malicious actor goes between two parties (e.g. mobile app & web site) & gains access to private information
Phishing Attack
(1) Email you with bad attachment or web link;
(2) Call you on the phone to obtain personal information or money, or
(3) Convince you to download something bad off of a website
Ramsomware Attack
Ransomware is a type of malware that encrypts data / files / folders preventing or limiting users from access and the cyber criminals ask for ransom.

Rogue USB Attack
Give-away USB thumb drive installed with malware or the malicious code makes used of USB flaw. Refer to the reference list for more details.

Rogue WiFi Attack
Either general data capturing at open wifi victims or targetted data capturing of VIP at semi-open wifi network like hotel.

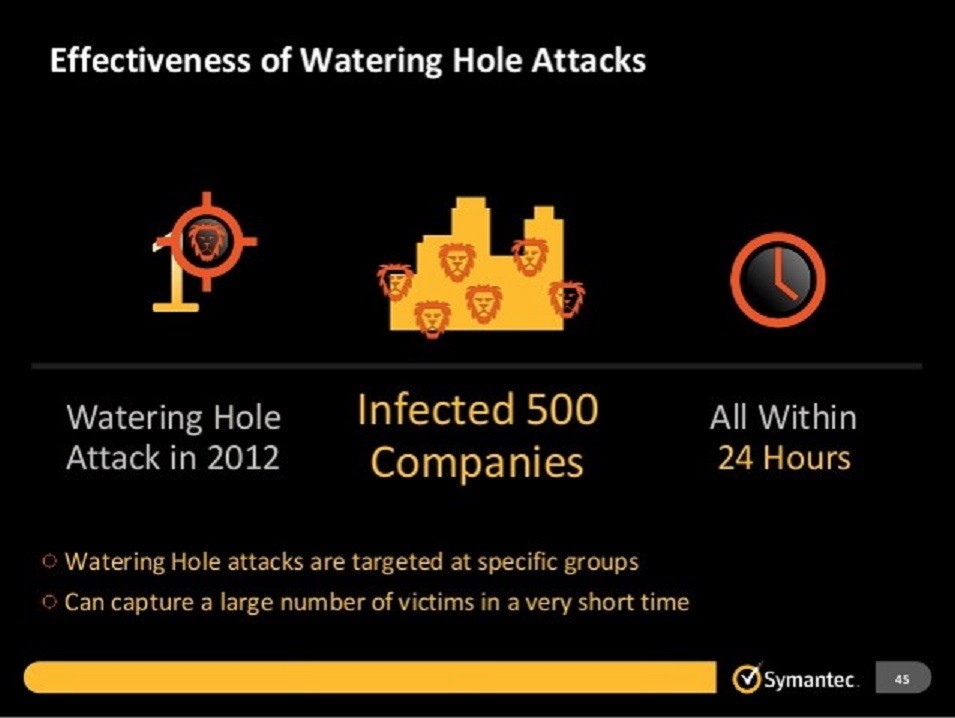
Waterhole Attack
Hackers take advantage of the fact that their targeted victims often meet or work at a particular physical or virtual location. Then they "poison" that location to achieve malicious objectives, say through fake wifi, VIPs favourite website, fake waitress, simple overhearing, etc.
Website Redirection Attack
Hidden scripts or iframes being injected into legitimate, but compromised websites, to redirect their visitors to the actual attack page.
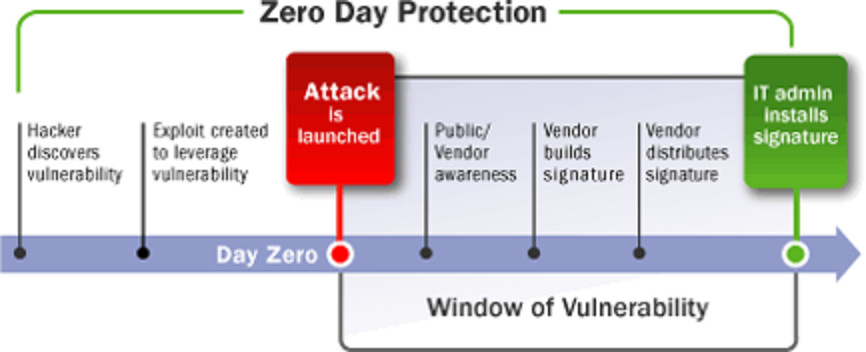
Zero Day Attack
A hole (vulnerability) in software that is unknown to the vendor. This security hole is then exploited by hackers before the vendor becomes aware and hurries to fix it — this exploit is called a zero day attack.
References
[1] 7 sneak attacks used by today's most devious hackers. Retrieved on 27 Jan 2015 from
http://www.infoworld.com/article/2610239/malware/7-sneak-attacks-used-by-today-s-most-devious-hackers.html
[2] Chinese hackers steal Indian Navy secrets with thumbdrive virus. Retrieved on 27 Jan 2015 from http://arstechnica.com/security/2012/07/chinese-hackers-steal-indian-navy-secrets-with-thumbdrive-virus/
[3] DarkHotel: A Sophisticated New Hacking Attack Targets High-Profile Hotel Guests. Retrieved on 27 Jan 2015 from http://www.wired.com/2014/11/darkhotel-malware/
[4] The Unpatchable Malware That Infects USBs Is Now on the Loose. Retrieved on 27 Jan 2015 from http://www.wired.com/2014/10/code-published-for-unfixable-usb-attack/

