Why Cybersecurity Is a Losing Game
KEY PLAYERS OF CYBER ATTACKS
In the recent publication of MIT Technology Review on "Cyber Attacks"[1], among other things cyber criminals, cyber-spies, hacktivists, and state-sponsored actors are key players.
NINE CYBER ATTACK PATTERNS
Nine classification patterns covered the majority (92%) of 100,000 security incidents of past 10 years, according to Verizon's 2013 study [2].
The basic patterns are listed below.
1. Point of Sales Intrusions
2. Web Application Attacks
3. Insider and Privilege Misuse
4. Physical Theft and Loss
5. Crimeware
6. Payment Card Skimmers
7. Cyber Espionage
8. Denial of Service
9. Miscellaneous Errors
LOSING GAME
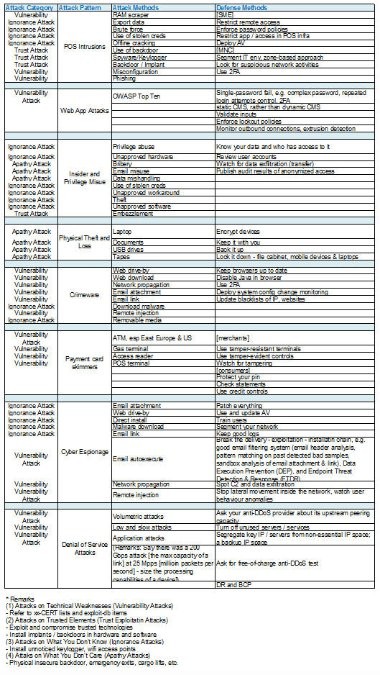
Four main cyber attack categories can be mapped to the nine attack patterns (see Appendix)
1. Attacks on Technical Weaknesses (Vulnerability Attacks)
- Refer to xx-CERT lists and exploit-db items
2. Attacks on Trusted Elements (Trust Exploitation Attacks)
- Install implants / backdoors in hardware and software
3. Attacks on What You Don't Know (Ignorance Attacks)
- Install unnoticed keylogger, wifi access points
4. Attacks on What You Don't Care (Apathy Attacks)
- Physical insecure backdoor, emergency exits, cargo lifts, etc.
Most of our current cyber security models and tools focus on Vulnerability Attacks and pay insufficient attention to Trust Exploitation Attacks, Ignorance Attacks and Apathy Attacks. The cyber attackers will continue to exploit the weakest links of technology and people.
REFERENCES
[1] http://www.technologyreview.com/view/528861/cyber-attacks/
[2] http://www.verizonenterprise.com/resources/reports/rp_data-breach-investigations-report-2013_en_xg.pdf
APPENDIX