Trust No One? How Far Forrester's "Zero Trust" Model Should Go
What is Forrester's Zero Trust Model?
Trust no one, not even your end users: That's the underlying theme of a new security model proposed by Forrester Research called "Zero Trust," which calls for enterprises to inspect all network traffic, from the outside and on the inside. It means inspecting all traffic in real time. The relevant network architecture would deploy what Forrester calls a network segmentation gateway. It's like a UTM [unified threat management] tool or firewall on steroids. It's a new security paradigm, Forrester claims.
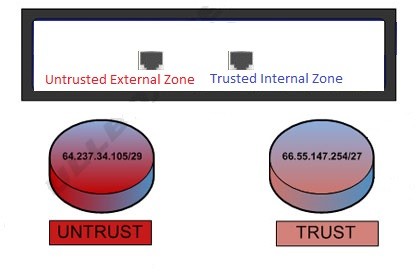
From the Trust-Untrust Conventional Model
Forrester argues the irrelevance of the "conventional" Trust-Untrust model, that is Trusted Internal Zone and Untrusted External Zone.
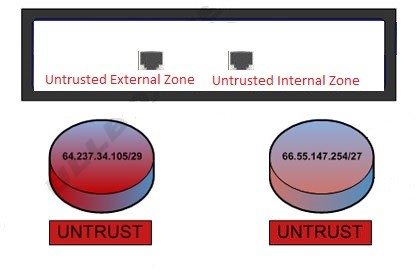
To the Untrust-Untrust New Model
Instead Forrester carries on to suggest the new Zero Trust Model, that is Untrusted Internal Zone and Untrusted External Zone.
Pandora's Box
If we extend Forrester's Zero Trust Model from different IT Security Zones to IT Hardware Value Chain and Software Value Chain, we can immediately see the damaging effects of opening up the Panadora's box. Are we not going to trust the inputs (hardware ICs, software libraries, etc.) and the final products (PCs, software systems)?

Trust Rebuild - Independent Assessment and Certification based on International Standard
At its simplest, "conformity assessment" means checking that products, materials, services, systems or people measure up to the specifications of a relevant standard. For example, a customer may want to check that the product he or she ordered from a supplier meets the purpose for which it is required. One of the most efficient ways to do this is when the specifications of the product have been defined in an international standard or industry-wide accepted blueprint.

References
"Forrester Pushes 'Zero Trust' Model For Security" retrieved on 8 Feb 2015 from http://www.darkreading.com/attacks-breaches/forrester-pushes-zero-trust-model-for-security/d/d-id/1134373?
"Conformity assessment and certification" retrieved on 8 Feb 2015 from http://www.iso.org/iso/home/faqs/faqs_conformity_assessment_and_certification.htm

