Protecting Intellectual Property: a Cybersecurity Perspective
Protecting Intellectual Property: a Cybersecurity Perspective
Intellectual property includes copyrights, trademarks, patents and trade secrets.
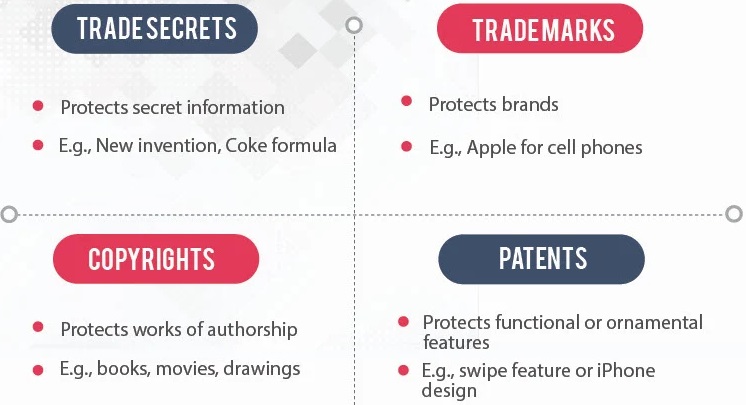
Protecting Intellectual Property
Proposed solutions to cyber-enabled intellectual property crime include criminal justice efforts, technical solutions to limit unauthorized access to intellectual property, and education campaigns.
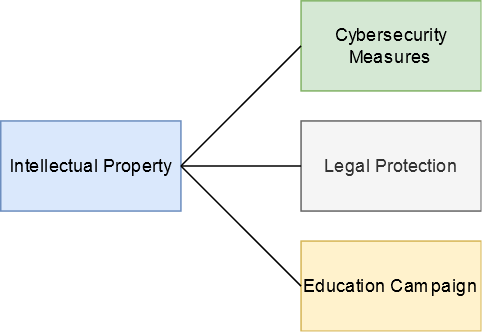
Cyber Attacks and Defenses on Intellectual Property

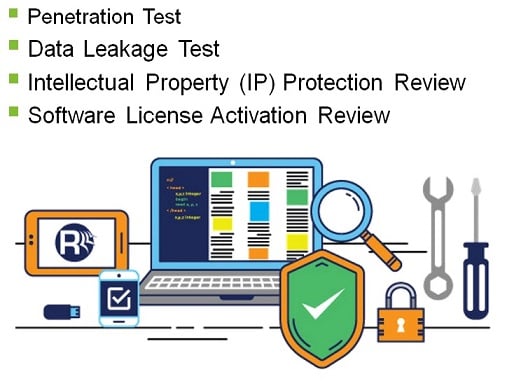
Cybersecurity Measure – Product Testing
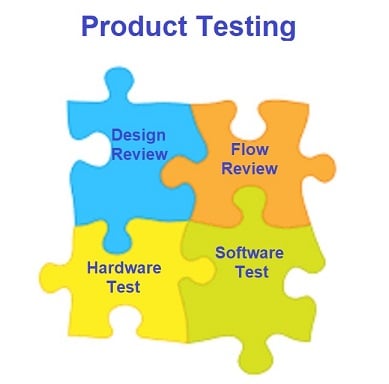
- Design Review: Consider requirements of the business, users and systems. Also it is essential referring to international standards and industry best practices.
- Flow Review: Review work flow for any defects or vulnerabilities that can be exploited by hackers or criminals.
- Hardware Test: Test the outfit against tampering. Test the firmware and test the whole entity and components for vulnerabilities.
- Software Test: Carry out vulnerability scanning & penetration testing. Test against data leakage, intellectual property compromise and software activation security.
Design Review

Flow Review
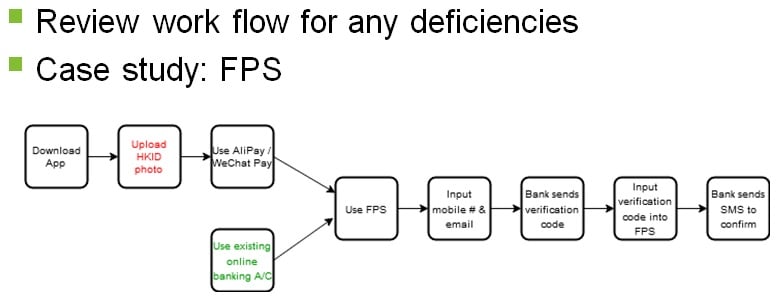
Hardware Test

Software Test
References
[1] www.unodc.org/e4j/en/cybercrime/module-11/key-issues/types-of-intellectual-property.html
[2] www.isysl.net

