New Ways to Hack and Protect Millions of Android Devices Remotely
In the beginning ...
The nightmare story goes like this - a recently discovered critical flaw resides in a core Android component called "Stagefright," a native Android media playback library used by Android to process, record and play multimedia files. Recently security researchers have found that there are several ways to hack millions of Android phones by exploiting the Stagefright vulnerability.
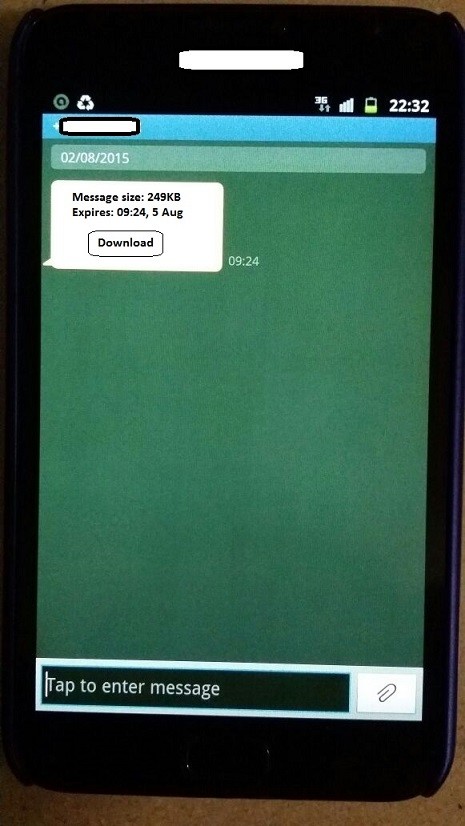
(1) Send malicious multimedia messages (MMS) to specific phone numbers
To Exploit Stagefright vulnerability, which is actively being exploited in the wild, all an attacker needs is your phone number to send a malicious MMS message and compromise your Android device without your interaction; no indication is required from your side.
Quick-Win Self Defense:
Turn off Auto-retrieve in your Android phone
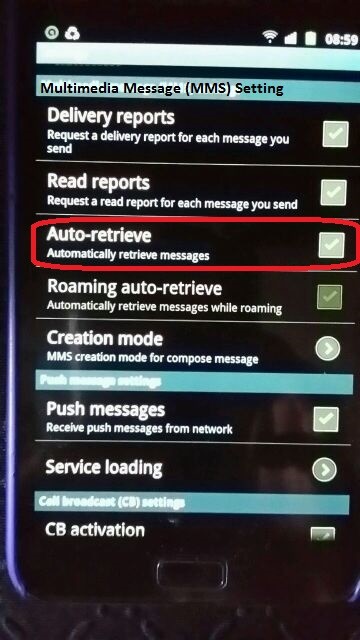
The user will not be automatically affected by malicious MMS Stagefright attack.
(2) Trigger Exploit from Android Application
Another new way exploits Android phone is based on a specially crafted MP4 file which will cause mediaserver's heap to be destroyed or exploited.
(3) Crafted HTML exploit to target visitors of a website
The hackers embed the malformed MP4 file into an HTML file, which is then uploaded to a web server to trap victims.
IMPACTS of AttackVectors 2 and 3
a) Hack millions of Android devices, without knowing their phone numbers and spending a penny.
b) Steal Massive Amount of data.
c) Built botnet networks of Hacked Android Devices, etc.
New attack vectors 2 and 3 require user interaction to either download the malicious Android app or land the victims on the specially crafted web page.
Quick-Win Self Defense against Vectors 2 & 3
1. Avoid downloading untrusted Android apps;
2. Avoid clicking untrusted links and land on malicious websites
Longer Term Solutions
Google has delivered a patch for Stagefright attack but it is not known how long the handset manufacturers and carriers will roll out patches to vulnerable millions of Android devices.
Google may need to push the patches through other channels or work through closer partnership with mobile security companies.

