How to Stop Malware Attacks on SCADA Systems
Lessons Learned from SCADA Malware Attacks
Stuxnet, Duqu and Flame are high-profile malware attacking industrial control systems and related supervisory control and data acquisition (SCADA) systems. From these lessons learned on how they attack and affect the systems we try to gain more understanding of SCADA cybersecurity measures.
2010 - Stuxnet
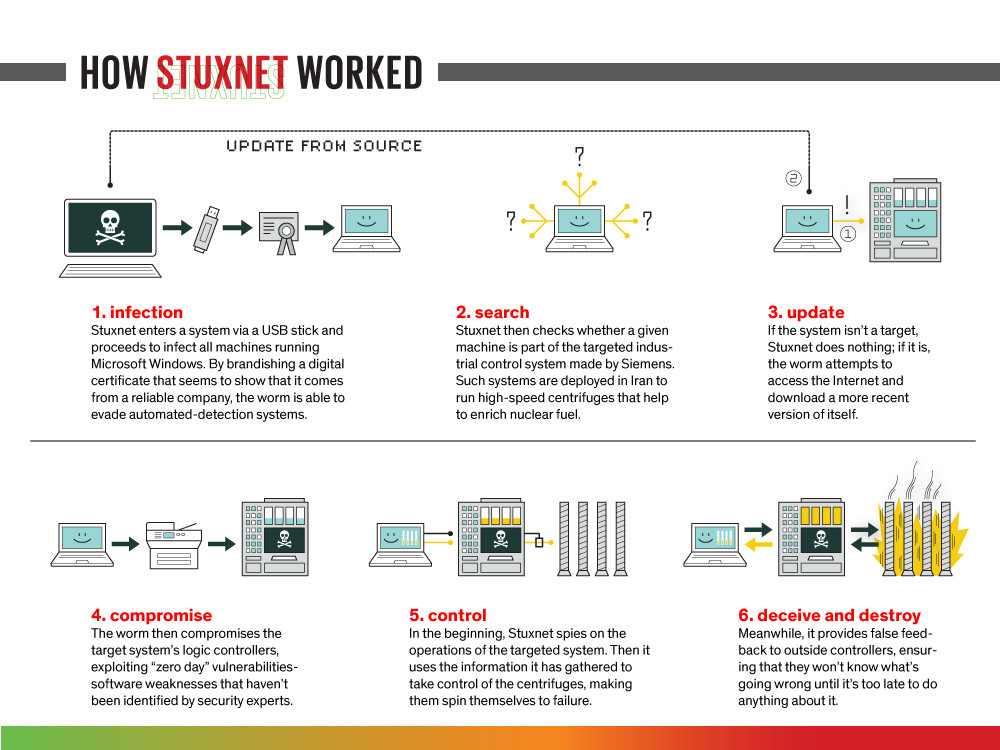
Stuxnet made headlines in June 2010 after it went to disable programmable logic controllers (PLC) and Siemens SCADA systems in Iranian nuclear power plants. It ranks as perhaps the most intricate and ingenious example of malware ever discovered. Not long after Stuxnet was detected and analyzed by software security specialists, it became apparent that it was the product of a well-funded, highly efficient entity.
Stuxnet was very effective because it exploited four zero-day Windows vulnerabilities. It was reportedly introduced to the target environment via USB flash drives planted either by an undercover agent or by unwitting power plant employees. Once it had access to a network, Stuxnet could identify and infect the hosts that managed SCADA systems controlled Siemens software. Microsoft and Siemens subsequently released patches to counteract Stuxnet, but not before considerable damage had been done, particularly within Iran.
Stuxnet Summary
Infection method - USB stick and fraudulent
Impact - PLC & Siemens SCADA disabling of nuclear power plants
2011 - Duqu
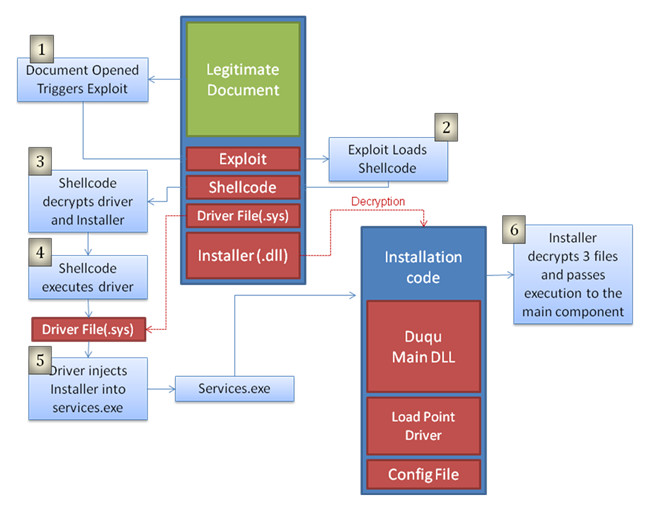
The Duqu worm was first detected in 2011. Malware analysts quickly noticed that it shared a lot of the same code with Stuxnet, but Duqu was designed for data surveillance and other intelligence efforts rather than the disabling of industrial systems. Like Stuxnet it seemed to target Iranian computers but Duqu did not focus on industrial or critical infrastructures. Like Stuxnet, Duqu is a complicated program as it seeks to exploit zero day Windows kernel vulnerabilities. Additionally it uses stolen digital certificates, installs a backdoor, and captures keystrokes. When Duqu installs itself, it uses a Microsoft Word file that exploits the TrueType font parsing engine that allows code execution.
Duqu Summary
Infection method - Word file opened to trigger exploit
Impact - data surveillance
2012 - Flame
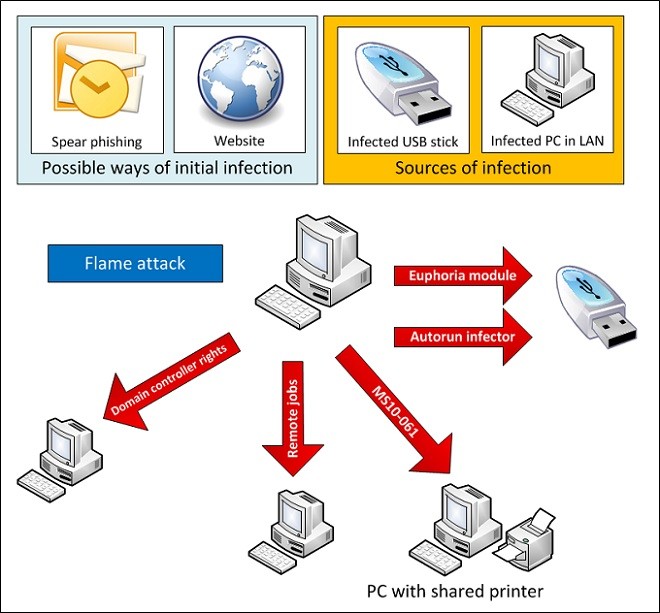
Flame was discovered in May 2012 by Kaspersky Labs. Most of the infections were in Iran, therefore it is not surprising that Flame shares characteristics with Stuxnet and Duqu (it also surfaced in Israel, Sudan, Syria, Lebanon, Saudi Arabia, and Egypt). Like Duqu, Flame seems designed for espionage rather than host disabling or data destruction. Flame uses a fraudulent digital certificate and spreads via USB stick, phishing email, malicious website, and infected PC in local network. Flame can exploit shared printer spool vulnerability and leaves a backdoor on computers. It can sniff network traffic and record audio, screenshots, Skype conversations, and keystrokes, as well as download information from other devices via Bluetooth. Flame determines which antivirus application is installed and then customizes its behaviour to minimize the probability of detection (for example, by changing the file name extensions it uses). Interestingly, Flame operators have the ability to send a “kill” command which searches for every trace of Flame on the infected host, including screenshots and data stolen by the malware, and eliminates them.
Flame Summary
Infection method - USB stick, phishing email, malicious website and fraudulent digital certificate
Impact - data collection and espionage
SCADA Cybersecurity Measures
Quick Wins
1. Restrict USB connection to PC and industrial control devices
2. Restrict direct Internet access from industrial control devices
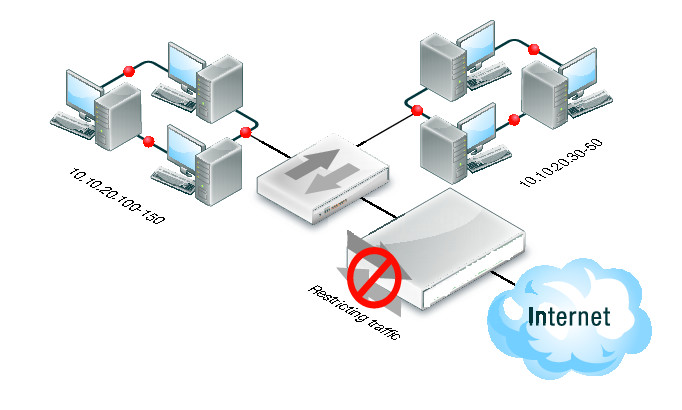
3. Control communications between industrial control network, remote access and corporate network
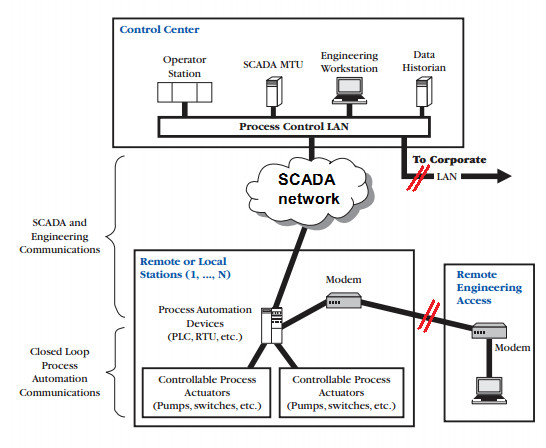
4. Control email services inside SCADA

Longer Term Measures
1. Review SCADA cybersecurity policy with reference to international standard like ISA-99

2. Revisit SCADA cybersecurity design & implementation
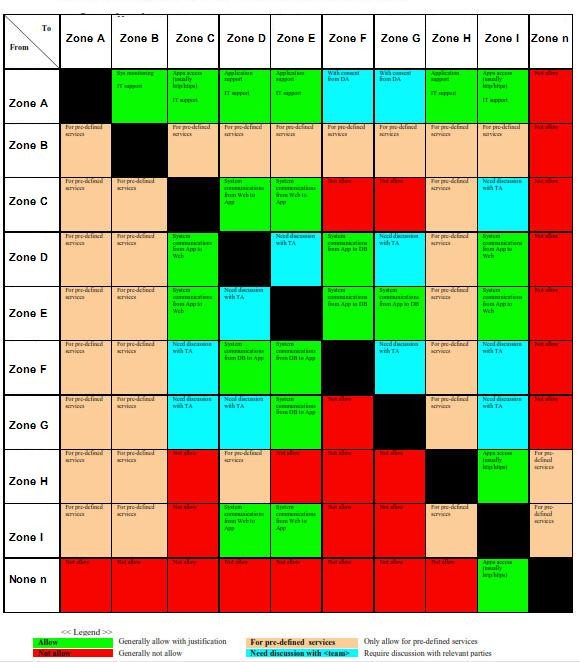
2.1 ISA-99 Zone and Conduit Design
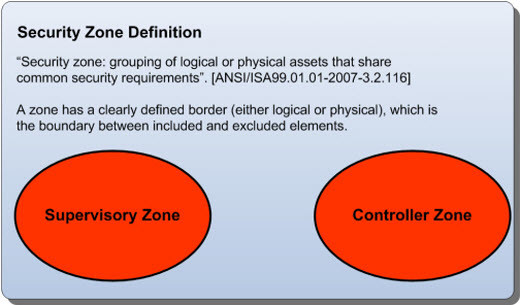
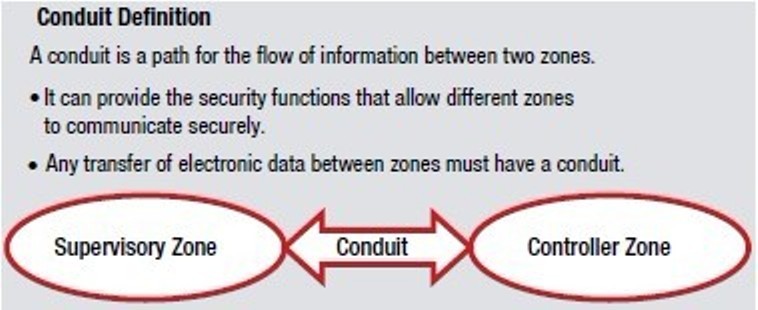
2.2 Overall Review
References
Stuxnet
Arstechnica.com, Confirmed: US and Israel created Stuxnet, lost control over it
Arstechnica.com, Stuxnet v0.5 Beta examined
Computerworld.com, Is Stuxnet the “best” malware ever?
Eset.com, In-depth analysis of Flame, Duqu, and Stuxnet mssecmgr.ocx
ForeignPolicy.com, Stuxnet’s Secret Twin
InfoSecInstitute.com, Installation, Injection, and Mitigation of the Stuxnet worm
Mediafire.com, Stuxnet source code
Networkworld.com, Siemens industrial software still full of holes
Net-Sec.org, Stuxnet was planted via infected memory stick
SCmagazine.com, Stuxnet infected Russian nuclear plant
Securelist.com, The echo of Stuxnet
Spectrum.ieee.org, The real story of Stuxnet
Symantec.com, W32.Stuxnet dossier (.pdf)
Wired.com, Iran: Malware sabotaged uranium centrifuges
Duqu
Arstechnica.com, Microsoft pushes out emergency fix to block Duqu zero-day exploit
Darkreading.com, Same toolkit spawned Stuxnet, Duqu, and other campaigns
Securelist.com, The mystery of Duqu framework solved
Symantec.com, Duqu: status updates including installer with zero-day exploit found
Techworld.com, Duqu Trojan written in mystery programming language
Flame
Arstechnica.com, Why antivirus companies like mine failed to catch Flame and Stuxnet
BBC.com, Flame malware makers send ‘suicide’ note
Networkworld.com, Kaspersky researcher cracks Flame malware password
Securelist.com, Back to Stuxnet: the missing link to Flame
UVA.nl, Reconstructing the Cryptanalytic Attack behind the Flame Malware (PDF; 832 KB)
Wired.com, Meet Flame, the massive spy malware infiltrating Iranian computers
ZDnet.com, Flame cyber-espionage dates back to 2006
ISA-99
The International Society of Automation, https://www.isa.org/

