The Changing Faces of Malware
What Is Malware Anyway?
Malicious software (malware) is a name given to a variety of software designed to interfere with the normal functioning of a single computer, server or a computer network.
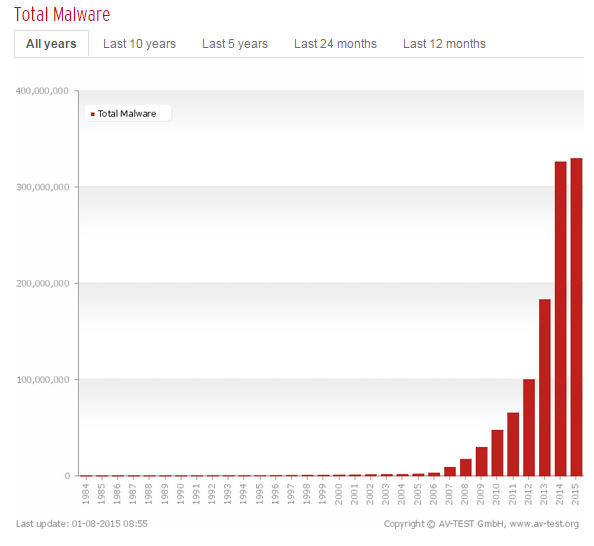
Changes in Quantity
We can witness a rapid growth of malware in the last decade.
Changes in How Malware Is Prepared
a) Basic Scripting & Programming (Pre-1990)
Early computer worm "Creeper" was created by Robert H. Thomas in 1971, the program copied into other machines through ARPANET.
In 1981 a boot sector virus "Elk cloner" spread by floppy disk fo Apple II.
In 1986 "Brain" MS-DOS based virus was spread out.
In 1987 there were quite a few viruses released - Win32.Worm.Suriv.A, Cascade.1701, Leigh, etc.
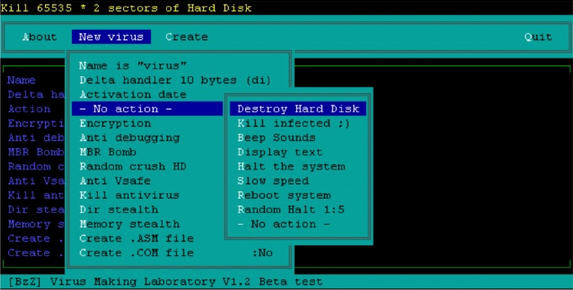
b) Crimeware Development Tool Kits (1990 - 2006)
There were a several basic tool kits like GenVir in 1990, Virus Creation Laboratory (VCL) in 1992, and Phalcon/Skism Mass-Produced Code Generator (PS-MP) in 1993.
c) Crime as a service (2007 - now)
Crime-as-a-service the new criminal business model
A professional, continuously evolving, service based criminal industry drives the innovation of tools and methods used by criminals and facilitates the digital underground through a multitude of complementary services, extending attack capacity to those otherwise lacking the skills or capabilities. Refer to http://www.scmagazineuk.com/cybercrime-as-a-service-the-new-criminal-business-model/article/374124/
Super Malware as a Key Tool
Malware is becoming increasingly sophisticated, intelligent, versatile, available, and is affecting a broader range of targets and devices.
Case Study 1 - Regin 2014
An advanced piece of malware, known as Regin, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen. Customizable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organizations, infrastructure operators, businesses, researchers, and private individuals.
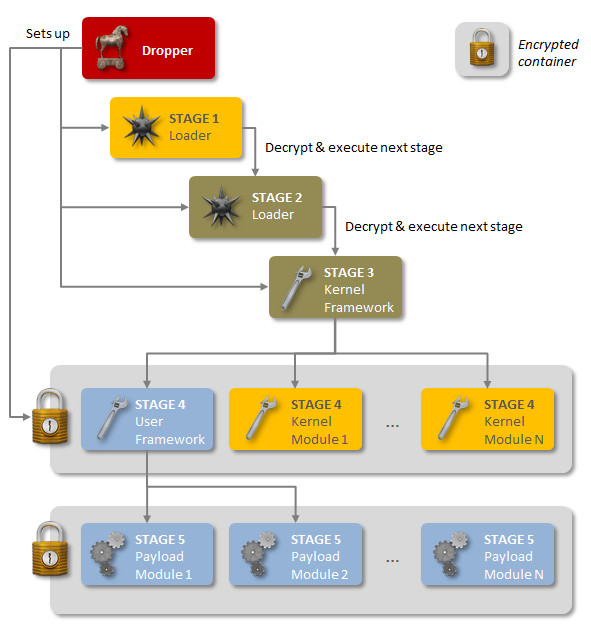
Refer to http://www.symantec.com/connect/blogs/regin-top-tier-espionage-tool-enables-stealthy-surveillance
Case Study 2 - Cryptolocker 2013
Spread through email attachments, this ransomware has been seen targeting companies through phishing attacks. Cryptolocker will encrypt users’ files using asymmetric encryption, which requires both a public and private key.
The public key is used to encrypt and verify data, while private key is used for decryption, each the inverse of the other.
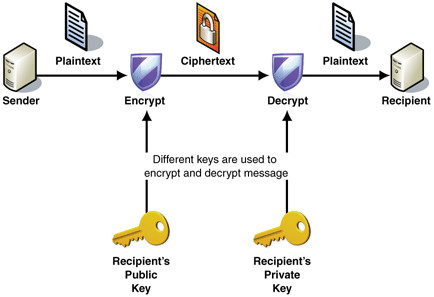
Refer to https://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/
Case Study 3 - Zeus 2007 and its variants till now
Zeus or Zbot is one of the most notorious and widely-spread information stealing Trojans in existence. Zeus is primarily targeted at financial data theft; its effectiveness has lead to the loss of millions worldwide. The spectrum of those impacted by Zbot infections ranges from individuals who have had their banking details compromised, to large public order departments of prominent western governments.
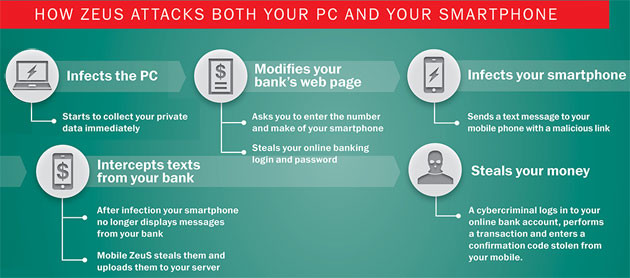
Refer to http://malaysiaitfair.com.my/?p=6648
Conclusion
We see increasingly sophisticated malware and the crime-as-a-service business model. The 2014 Internet Organised Crime Threat Assessment (iOCTA) Report suggests the following:
- Improved general awareness
- Improved capacity building and training of cybersecurity professionals
- Joint partnerships in combating malware and its new business models

