Bypassing Firewalls and Avoiding Detection in Penetration Testing
Now You See Me and You Don't
Penetration testing used to be a joyful journey. It is to look for security weaknesses in network, hosts, applications and data access.
Paradise Lost

The paradise has been lost when the penetration tester hit into a web application firewall (WAF). His favorable tools like Nessus and Acunetix turn to a state of helplessness.
Detecting Web Application Firewall – wafw00f
One way to detect web application firewall is to use Web Application Firewall Detection Tool, wafwoof. That is pre-installed in Kali Linux.
When you get to the appropriate directory /usr/bin in this case, simply issue the command for the target website:
# wafw00f [target website]
REMINDER – only test the website that you are allowed to, period.
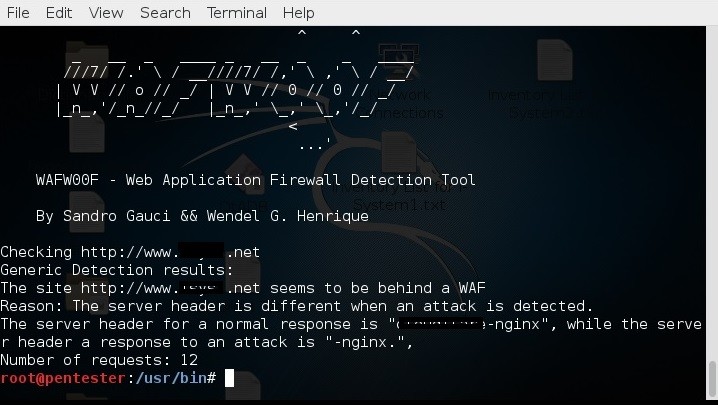
Too bad, WAF is detected.
For the sake of discussion try another target website.
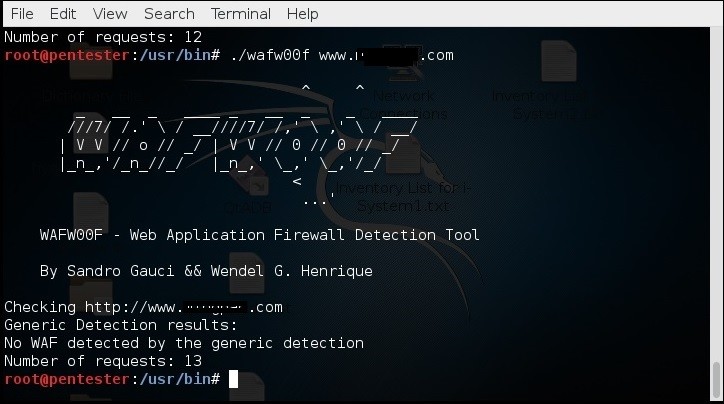
No WAF is detected for this second website.
Testing WAF bypass and getting to the target – hping3
We can test the bypass using the tool hping3, which is also pre-installed in Kali Linux.
# hping3 –c 10 –S –spoof [spoofing IP] –p 80 [target website IP]
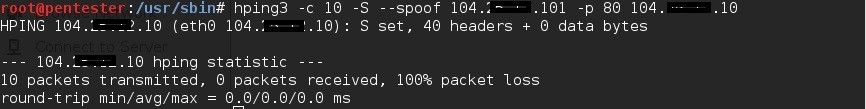
No luck.
Try again.
# hping3 –S [target website IP] –c 80 –p ++1
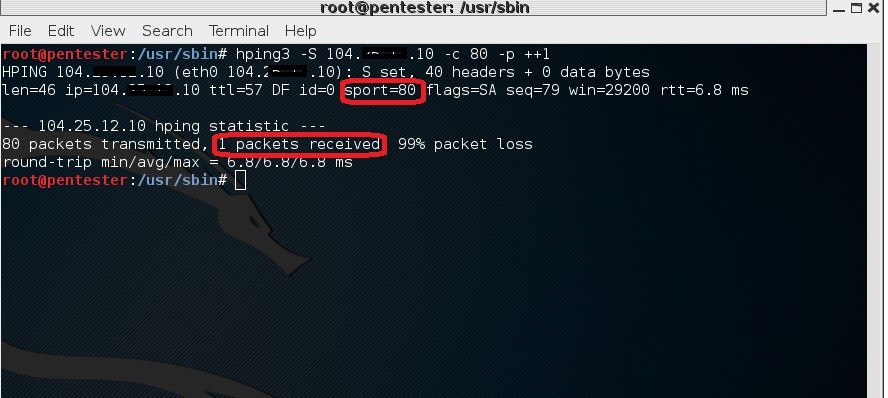
One packet gets through WAF via port 80 to the target website.
Second tool to bypass WAF – nmap’s firewalker
Nmap is pre-installed in Kali Linux as well.
# nmap --script=firewalk --traceroute [target website IP]
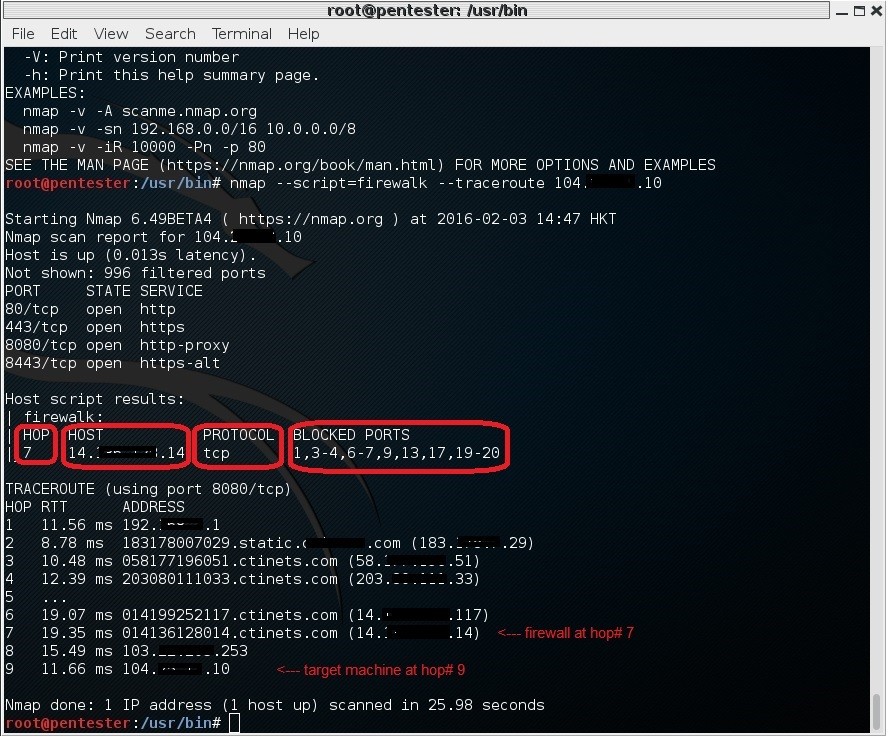
This time we find WAF sitting at hop# 7 with ports 1, 3, 4, 6, 7, 9, 13, 17, 19 and 20 blocked and there are 996 ports filtered.
Ports 80, 443, 8000 and 8443 are open.
Thank you and welcome.

